VOSYSVirtualNet, a Low-latency Inter-world Network Channel for Mixed-criticality Systems

Integrating multiple subsystems with different levels of criticality is an efficient solution in a number of domains (e.g., automotive, avionics, IIoT, real-time aware systems, etc.). To ensure the proper temporal and spatial isolation, a highly privileged software component, VOSYSmonitor, is deployed to orchestrate the subsystems; it enables the co-execution of two operating systems on a single System on Chip - A rich operating system, such as Linux, along with a safety critical operating system, fully isolated from each other using ARM TrustZone.
However, a closer look at specific scenarios reveals that a communication between the two operating systems is needed.
A powerful Virtual Open Systems design for a simple implementation
VOSYSVirtualNet is just the right solution to enable this communication link by providing a low-latency inter-world network channel. Its versatile design is built around already existing primitives in both worlds, only demanding for implementing the physical layer of the network channel.
This ensures a low complexity, meaning only minor modifications have to be made to the operating systems running in the Secure and Non-secure world. VOSYSVirtualNet ensures fast reaction due to a very low latency of the network link. Moreover, it provides security features to mitigate common network attacks.
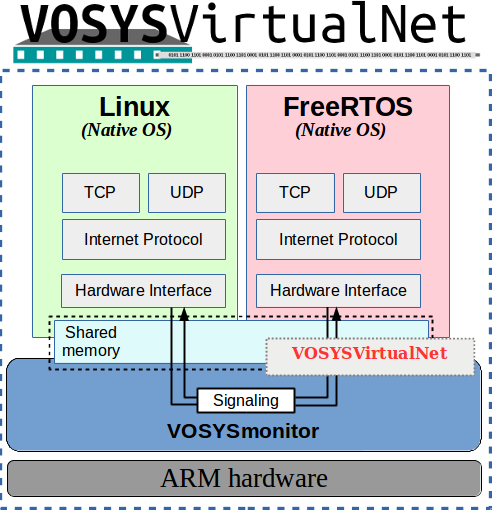
VOSYSVirtualNet System Overview
VOSYSVirtualNet main features:
- Versatile system design
- Lightweight implementation
- Compatible with different embedded IP stacks (e.g. FreeRTOS+TCP, lwIP)
- Resource usage efficient
- Protection against malicious attacks
Technical insights
VOSYSVirtualNet enables the exchange of data between two entities consolidated on top of VOSYSmonitor (one running in the Secure and another one running in the Non-secure world). The underlying mechanism that enables this functionality consists of two shared buffers located in RAM. Although the buffers content is not specified or bound to specific content type, the VOSYSVirtualNet mechanism is tightly coupled to the exchange of network packets based on existing IP stacks available in both entities.
Both systems (Secure and Non-secure) rely on a system driver that handles a number of operations on behalf of the communication entities, e.g., providing a communication endpoint to send and receive data and providing means to signal the other communication entity about new content in its transmission buffer. The signaling involves communication with VOSYSmonitor via its SMC-call interface.
Security features
VOSYSVirtualNet is meant to be integrated into a safety critical environment| based on VOSYSmonitor. Therefore, it is important that malicious or erroneous applications in the non-critical system (i.e., Normal world) cannot affect critical components running in the Secure world. VOSYSVirtualNet has been enhanced with additional counter-measures to mitigate the most common vulnerabilities such as:
- Denial-of Service: A non-critical system sends requests at such a high rate that the critical system is only able to serve the adversaries requests, without the ability to perform any other tasks.
- Memory corruption: A non-critical application allocates a buffer at the boundary of the Secure world memory plan in order to provoke overwriting of critical system.
- Packet corruption: Networks packets sent by non-critical system are corrupted by a malicious application.
- Kvm performance
- Virtual bfq
- Vosyshmem zerocopy
- Vosysmonitor
- Api remoting
- Vosyswitch nfv virtual switch
- Accelerators virtualization interface
- Vosysmonitor jp 日本語
- Vosysmonitorx86 jp 日本語
- Vosysiot edge
- Vfpgamanager
- Vosysmcs
- Vosystrustedvim
- Vosysmonitor sossl framework
- Vosysmonitorx86
- Vosysmonitorv risc v
- Vosysmonitorv risc v jp 日本語
- vosysvirtualnet jp 日本語
- Vosyszator
- Vmanager
 VOSySofficial
VOSySofficial