VOSySmonitor - Secure Operating System Service Layer Generation Framework

Virtual Open Systems proposes VOSySmonitor, a powerful software product solution, that runs in the Secure Monitor mode of ARM processors in order to enable the concurrent execution of systems with different criticality levels on a single platform. VOSySmonitor provides full spatial and temporal isolation among each domain by using the hardware security extensions called ARM TrustZone. The principle of TrustZone management is to partition system resources (hard-wired or configurable) into Secure and Non-secure regions, so that a secure protection is ensured by monitoring physical access to memory or peripherals; a system running in the Secure world is therefore totally isolated from applications executing in the Non-secure world.
VOSySmonitor manages the context switching between the two worlds by triggering a Secure Monitor Call (SMC) instruction or by hardware exception mechanisms, such as interrupts (e.g., FIQ, IRQ, External abort) in order to ensure a correct operation for each world. Last but not least, VOSySmonitor is ISO 26262 ASIL C certified, thus making the perfect solution for the modern Automotive eCockpit, where Vehicle information, entertainment, navigation, camera/video and device connectivity are being combined into displays.
The VOSySmonitor architecture is designed to ease the support of new hardware platforms, as well as the integration of Operating Systems in each world (Secure and Non-secure). Depending on the hardware requirements, VOSySmonitor can reuse software components, such as common peripheral drivers, in order to minimize the integration effort. Moreover, systems consolidated on top of VOSySmonitor can interact with VOSySmonitor (e.g. to request specific services) through a service layer (called "The Secure Operating System Service Layer (SOSSL)").
This communication interface is standardized but it can be extended for complex use-cases. Thus, it can be customized by the customer in order to provide the possibility to develop custom world interactions (e.g., interrupt handler, secure services, world context switching, etc.), extensions and new features. To ease this customization process, VOSySmonitor provides an intuitive framework (based on Python and YAML configuration files), which enables the automatic generation of the SOSSL depending on specific input parameters.
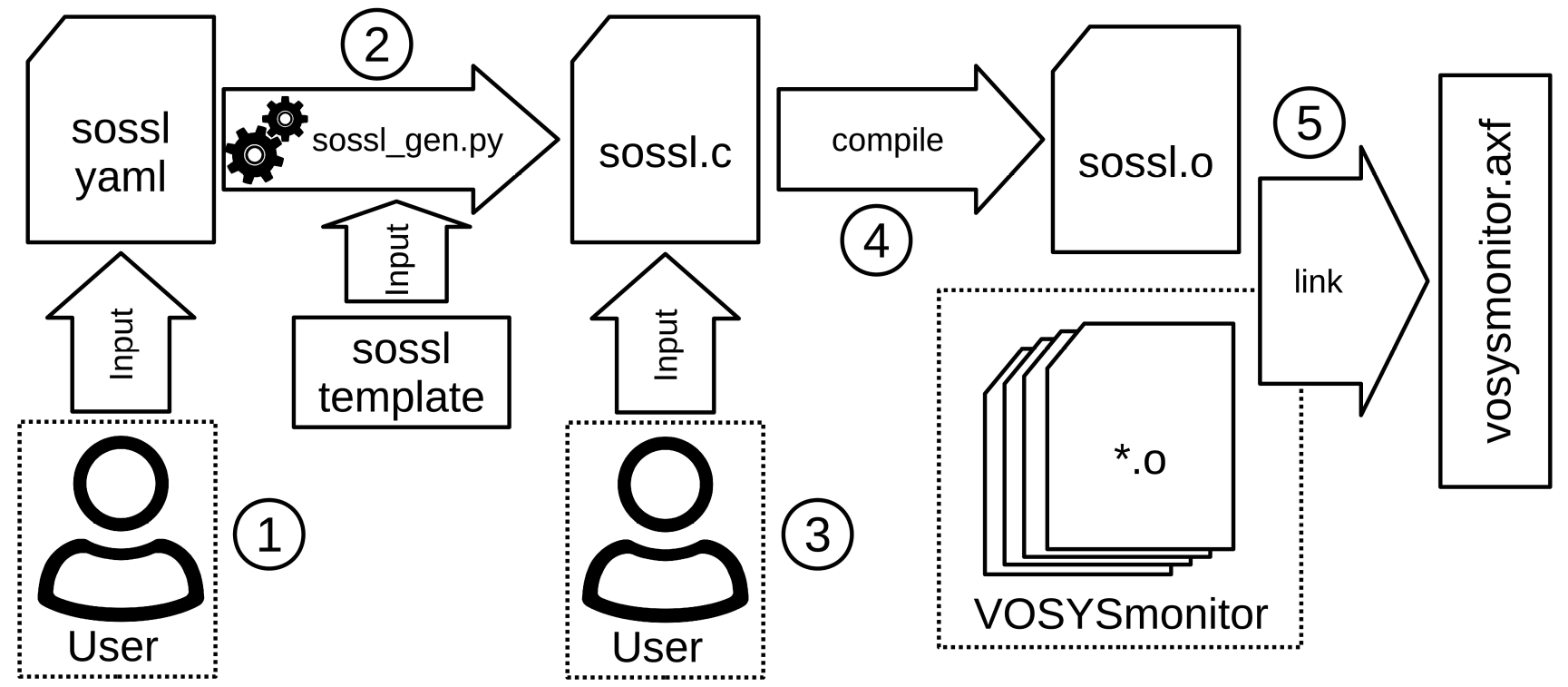
VOSySmonitor - Secure Operating System Service Layer Generation Framework Overview
SOSSL framework overview
The SOSSL generation framework is composed of several key components that interact together in order to configure and compile VOSySmonitor. In a first step, the user can set certain parameters to customize the SOSSL of VOSySmonitor by using a YAML configuration file. Then, the configuration file together with a template is fed into a Python application tool to generate the SOSSL C file. Once the SOSSL file is generated, the user can update/add certain features by directly modifying the SOSSL C file. Afterwards, the C file is compiled and linked with the other VOSySmonitor components to generate the final elf file for the target platform.
The configuration parameters of the SOSSL framework are split into three main keywords:
- The "Features" keyword allows the user to enable/disable or customize advanced features of VOSySmonitor itself. As a matter of fact, it allows to enable/disable VOSySVirtualNet (a safe and efficient inter-world communication channel integrated in VOSySmonitor) as well as configuring its security parameters such as the rate limiter; change the behaviour of the FPU context switching policy; enable/disable self tests, etc.
- The second keyword "Operating Systems" allows the user to change the behaviour of the operating systems that are consolidated on top of VOSySmonitor. Parameters such as Entry Point, Entry Exception Level (e.g., hypervisor-EL2, kernel-EL1, etc), Endianness, Migration Capacity, etc. enable the user to exactly adjust the behaviour and manipulate the execution of the given OS to the needs of the user.
- The third keyword, called "SMC Services", allows the user to define new custom SMC services in the SOSSL C file of VOSySmonior. Such custom services can be very precisely defined towards the users needs. For example, it can be defined whether the given service is callable from the Secure or Non-secure (or both), how many arguments the SMC service returns, with which SMC ID the service is callable, etc. The SOSSL framework then creates a code skeleton for the specified service that is accessible by the user to implement the service directly in the generated C file.
VOSySmonitor SOSSL features
The main features of the Secure OS Service Layer are:
- Easily understandable based on YAML and Python3/Jinja2
- Consolidated Operating Systems are fully customizable (e.g. entry point, 32 or 64bit, endianess, etc.)
- Fully customizable CPU core assignment for different Operating Systems
- Definition of new SMC-based services
- Enabling of VOSySmonitor features (e.g. performance profiling, system health monitoring, etc.)
- Easily extensible
Virtual Open Systems Contact
For any inquiry related to VOSySmonitor product and custom porting services you can contact us.
- Virtual bfq
- Kvm performance
- Vosyshmem zerocopy
- Vosysmonitor
- Api remoting
- Vosyswitch nfv virtual switch
- Accelerators virtualization interface
- Vosysmonitor jp 日本語
- Vosysmonitorx86 jp 日本語
- Vosysiot edge
- Vfpgamanager
- Vosysvirtualnet
- Vosysmcs
- Vosystrustedvim
- Vosysmonitorv risc v
- Vosysmonitorx86
- Vosysmonitorv risc v jp 日本語
- vosysvirtualnet jp 日本語
- Vosyszator
 VOSySofficial
VOSySofficial