VOSySmonitor on Mediatek MT2712 Realizes Hypervisor-less Automotive eCockpit
Android Auto 9 In-Vehicle Infotainment and critical RTOS co-executed with VOSySmonitor on MT2712

VOSySmonitor is an ISO 26262 ASIL C certified safety-critical system partitioner built on ARM TrustZone that enables the concurrent execution of multiple operating systems with different levels of criticality. The innovative VOSySmonitor architecture splits the system in two main compartments, one for the safety critical and the other for standard applications, isolating them with the use of Arm TrustZone. Such isolation is of pivotal importance to provide security, with safety critical applications running fully protected (in a separate memory address space with tagged caches and isolated devices) from the standard applications. The VOSySmonitor software layer is positioned in the lowest level of the vehicle software stack (Arm monitor layer), providing strongest control on the system resources partitioning at best-in-class performance, while offering the most flexible system architecture.
VOSySmonitor is therefore the perfect solution for enabling the Automotive eCockpit next generation, where Vehicle information, entertainment, navigation, camera/video and device connectivity are being combined into displays, in modern vehicles without the cumbersome dependency of using expensive traditional type-1 hypervisors. Furthermore, VOSySmonitor does not impose any closed solution or dependent component and can be used in combination with open source technologies like Linux, Android, Automotive Grade Linux, etc., which allows to reduce costs by proposing a bottom-up solution, where Virtual Open Systems focuses on the isolation, safety and performances of critical resources.
- Simplified virtualized electronic control units: VOSySmonitor enables the execution of multiple operating systems on the same platform with no performance overhead, reducing hardware and wiring costs, easing software maintenance and prototyping.
- Highest security and safety: VOSySmonitor partitions the system resources isolating safety critical applications in a protected compartment. It is ISO 26262 ASIL C certified and supports security Trusted Execution Environment implementations, such for instance OPTEE.
- Scalability and openness: VOSySmonitor provides a scaleable solution with increasing complexity from simple use cases (for instance with Linux running with an RTOS) to ADAS applications with a high number of operating systems working together.
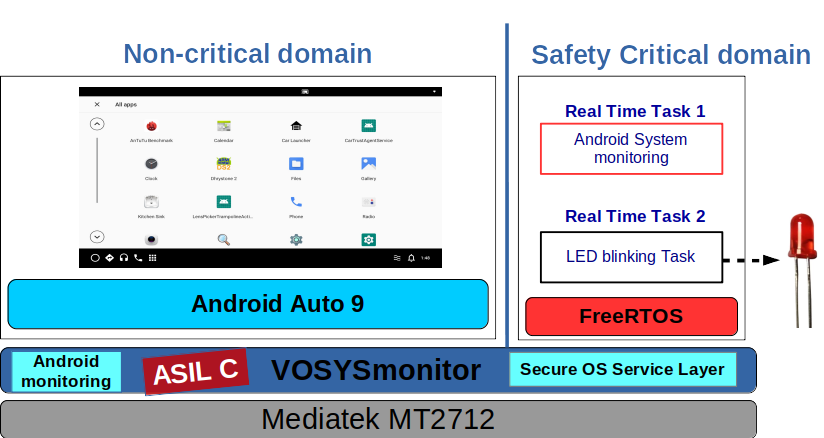
Android Auto 9 IVI and critical RTOS co-execution with VOSySmonitor on Mediatek MT2712
VOSySmonitor benchmarked performances on Mediatek MT2712
This video showcases an use-case example of VOSySmonitor application, where an IVI system (Android Auto 9) and a safety critical Real-Time Operating System (FreeRTOS) are executed on a Mediatek MT2712 platform (2 Cortex-A72 and 4 Cortex-A35). The main goal of this demonstrator is to showcase the high performance of VOSySmonitor and the freedom from interference between the Safety critical RTOS and Android Auto 9. Indeed, it is important to notice that VOSySmonitor ensures full isolation of the safety critical domain even in case of failure on the Android OS side.
- Safety critical domain - Fast boot: VOSySmonitor always starts the Safety critical domain first in order to meet stringent real-time constraints from the critical OS. It is important to notice that VOSySmonitor is a software layer that is executed before the Safety critical domain, which adds a small overhead in the full cold-boot time of the Safety critical domain compared to a native execution. However, VOSySmonitor has been developed to minimize this overhead as demonstrated with the hereinafter measurement; in fact the total cold-boot time is kept below 265ms, whichever the core selected by VOSySmonitor for scheduling the Safety critical OS (i.e., FreeRTOS): this value includes the VOSySmonitor setup time (corresponds to the execution time from the VOSySmonitor entry point to the FreeRTOS entry point), which is negligible at ~1ms.
- Safety critical domain freedom from interference: The design goal of VOSYSmonitor is to give the full priority to the Safety critical domain assigned in the Secure world in order to meet the real-time constraints. This means that the Android workload has no or insignificant impact on the responsiveness of Safety critical domain as the FIQ latency benchmark can prove. Indeed, the FIQ latency impact (Average: 1,6µs to 4,3µs) observed by varying the Android workload is only due to the cache eviction performed by Android operations, which might impact data used by VOSySmonitor and slightly vary the context switch time. However, it is important to notice that the context switch time is faster enough to be negligible from the Safety critical RTOS point of view. As a matter of fact, FreeRTOS is scheduled with a tick period of 2ms in this demonstrator, so, it means that the VOSySmonitor overhead represents no more than 0,5% in the worst case scenario (i.e., Maximum context switch value = 10,18µs).
- Android OS crash monitoring: VOSySmonitor is monitoring the Normal World execution to detect potential failures and to eventually inform the safety critical RTOS execution, running in the Secure world, about this failure. In addition, it is important to notice that VOSySmonitor ensures full isolation of the Safety Critical domain, therefore, the critical RTOS execution is not impacted by the crash of Android.
| Item | Description | Performance results |
|---|---|---|
| Safety critical OS boot time | Full boot time needed to enter in the Safety critical OS from a Power-On operation. | 265ms (including 1ms of VOSySmonitor setup time) |
| Safety critical OS FIQ latency | Overhead induced by VOSySmonitor context switch to forward an FIQ to Safety critical OS | Average = 1,6µs - 4,33µs |
| Android AnTuTu benchmark | Benchmarks for Android devices that test/stress several parts of a device and assigns a score |
|
| Android Drhystone benchmark | Computing benchmark (integer) that allows to measure the general CPU performance |
|
| Non-critical domain IRQ latency | IRQ latency of non-critical domain induced by prioritizing Safety critical domain execution |
|
VOSySmonitor benchmarked performances on Mediatek MT2712 platform
- Kvm on arndale exynos
- Kvm armv7 multiple guests poc
- Kvm full virtualization on vexpress
- Kvm vs tcg virtualized guests
- Byod android kvm on cortex-a15
- Kvm android guest on arm fastmodels
- Vosyshmem api remoting
- Virtual bfq in action
- Vosyswitch perf openstack integration
- Vosyswitch interop2017 shownet arm server
- Kvm virtualization training video
- Vosyswitch odp armv8
- Vosyswitch interop
- Vosysmonitor als2016
- Vosysmcs rcar forum 2018
- Vosysmonitor als2017
- Virtualizing fpga accelerators
- Memguard memtalk kvm armv8
- Vosysiot sido demo
- Vfpgamanager sdnnfv2018
- Vosysiot edge iotwc2018
- Vosysmonitor emcos ew2019
- Virtualizing stb lower tco
- Vosysmonitor mt2712 jp 日本語
- Vosysmonitor emcos ew2019 jp 日本語
- Vosysmonitor secure freertos optee linux
- Everest virtio fpga
- Vosysmonitorv risc v demo
- Vosysmonitorx86 demo
- Vosysmonitorv core sharing virtualization demo
- Wave fpga sriov
- Virtio loopback agl lf
- Virtio loopback agl lf alpha release
- Virtio loopback sound agl
- Risc v multiple os
- K8s svff satcom wave
 VOSySofficial
VOSySofficial